Virus dan Safe Mode
Safe mode? Yes ... Windows will usually be equipped with safe mode
mode. Meant that the user can fix Windows if there
a disaster. Windows safe mode Windows is actually nothing more than a
run with a standard driver! So if there is fretfulness on driverdriver
non-standard Windows that makes Windows standard mode fails
executed, the Windows standard mode can be recovered again by
go into safe mode mode. While in safe mode this mode, the user
opportunity to perform on the elimination of non-standard drives are problematic
them. In this way, Windows is damaged will be normal
back. That's expectations.
Looking at the function, of course, safe mode this mode, is also a threat
for the survival of viruses or programs that like to make
problem ... Therefore, the safe mode this mode is also the target
The main virus program. That is, the virus will try to manipulate the safe mode
 How to get into safe mode mode?
How to get into safe mode mode?
Perform reboot the computer. At the time of the process
starts booting, press the F8 key quickly and
repeatedly. (A little hysterical also be ... ☺) So
Windows boot menu appears. Choose Safe Mode, then
process will run until the end display options
user should use to get into Windows safe
mode. In Windows XP, the account will usually appear
Administrator and the accounts we have. Choose an ordinary user account
we use.
After that, usually we'll be asked whether to go into Safe mode mode
or are we going to use Windows system restore facility. Click Yes, then
we will go into Windows safe mode mode. That is, Windows will actively
with the device it is (minimum standard).
Repeatedly double-click the subkey that looks so these locations
was found.
On the Run subkey is usually the virus will write the name of a new value for
activate the virus program. To delete the existing data, click the value name
and press DEL.
Other locations that we need in order to check this registry autorun
are:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Once
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
OnceEx
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
If found the name of the value that you think are strange, delete it ...
From some of the subkeys above, there is a subkey that is quite special. namely
RunOnce subkey. Unlike the Run subkey that will always run
program is in it every time Windows is turned on, the subkey
RunOnce is typically used to run a program as much as one
time only! So, this subkey is usually used by a program to enable
the process as much as one-time only, so the name is written down value
here will only apply one time only. Once executed, the value name
will be deleted.
If the virus is quite naughty, he will create a virus program for writing
pengaktifnya in this subkey. Thus, the virus will be active when the computer is turned on.
The program will be run and the name of the trigger value will be deleted. then
he did not leave a trace in msconfig. After a time when the virus is active,
he will make the program a timer that periodically re-write the name value
in the subkey. Or maybe the virus will only write the data on
RunOnce subkey when the computer will be logged off. That way, the virus
will be maintained existence. Pretty clever ', right?
But .... There are even crazier ... ☺ RunOnce subkey with the help of this, the virus
would still be alive even if Windows is run in SAFE MODE mode!
The trick? It's simple! Namely by adding a certain character
on behalf of such value, then the virus will be run in safe mode.
Character is it? I will not tell you☺ heheh!
I think builders will hide the science anymore.
We direct the practice, yes? Call Regedit and go to the subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Once
We create a value named COBA's name. The name of this value for example
will call the virus file named VIRUSKU.EXE
Right-click the RunOnce subkey. Context menu will appear, select New, select
String Value.
A new subkey will appear. Let's change the name value with the data
COBA. Type in COBA and press Enter
Double-click the value name, and we fill it with data
c: \ windows \ virusku.exe. Then click OK.
If correct in doing so, we will have the name value with the COBA
type string and has the data c: \ windows \ virusku.exe. That is, when later
Windows is enabled, the file VIRUSKU.EXE will come running!
Now, how do you get the name value will still be
even run Windows included in SAFE MODE mode?
Easy! Simply add the character * (asterisks) in front of the name value.
That is, we replace with the name of COBA COBA name *
If you do not believe, do the boot and log in SAFE MODE mode.
Saharusnya VIRUSKU.EXE file with the name will still be run by
Windows. If we attach the file is a real virus file, then
consequences will be quite fatal. Virus will still be present in memory even if we have
mode using SAFE MODE. Even though this trick seems simple, but
quite dangerous if used. Because after the data is executed, then
run data will be deleted by Windows. so that will
complicates tracking the source of the problem. Take care ...!
If the virus remains active even if we had entered into
mode safe mode, check the RunOnce subkey is
over and over again. Who knows the virus is not the technique used by shell
spawn, but rely on the RunOnce subkey.
RunOnce this technique, it is still rarely done by the virus.
So, the obligatory pairing! The more
manipulation that can make the virus is active, it will
the more successful the virus survive. Viva Virus
Alternate Shell Safe Mode
The virus usually will not be active when we go into safe mode. That's usually!
In its development, the virus was also already started to widen
wings, grabbed (cease-and-desist .. ☺) some handling safe mode
by pairing the trigger file on some registry subkey. with
In this way, the virus will still be run and prevent users to enter
SAFE mode mode! Rude indeed! But yeah ... so .. my dear .. hehehe
☺
So, this trick will fulfill the first trick was to add intricately ... ☺
shutdown virus. Hehehe ... pa pa ndak even added fun, right?
Location attacked registry subkey is:
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Control \ safeboot
In this safeboot subkey will have a name value named
AlternateShell. With its data type is string. We'll see the default field
is cmd.exe. If it does not contain such data, it is possible that the file
there is a file virus. Beware!
Suppose it happens, double click the value name and the Value field
change to the data contains cmd.exe. Click on OK. Wrong!
That need attention! Viruses are generally also will attack subkeysubkey
are similar. The meaning is this ... will attack the virus is also the location of the registry
else that stores data safeboot, usually there are more than
one of these controls. Other locations are under attack are:
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet002 \ Control \ safeboot
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet003 \ Control \ safeboot
So, depending on how the computer has a subkey
ControlSet00X. X here represents the numbers 1, 2, and so on. by turning the
data on behalf AlternateShell value, then the computer will usually
failed to get into SAFE MODE, instead running a virus file!
If a virus attack and we fail to go into safe mode
mode, then the alternate shell subkey, this subkey must we
check out. If the data content strange, not standard, then change
filling with cmd.exe.
Despite this manipulation seem harsh and cruel, but
what can make, interception go into safe mode, shall
carried out. Because it will make the virus more secure and
maintained its existence!
Safe mode? Yes ... Windows will usually be equipped with safe mode
mode. Meant that the user can fix Windows if there
a disaster. Windows safe mode Windows is actually nothing more than a
run with a standard driver! So if there is fretfulness on driverdriver
non-standard Windows that makes Windows standard mode fails
executed, the Windows standard mode can be recovered again by
go into safe mode mode. While in safe mode this mode, the user
opportunity to perform on the elimination of non-standard drives are problematic
them. In this way, Windows is damaged will be normal
back. That's expectations.
Looking at the function, of course, safe mode this mode, is also a threat
for the survival of viruses or programs that like to make
problem ... Therefore, the safe mode this mode is also the target
The main virus program. That is, the virus will try to manipulate the safe mode
 How to get into safe mode mode?
How to get into safe mode mode?Perform reboot the computer. At the time of the process
starts booting, press the F8 key quickly and
repeatedly. (A little hysterical also be ... ☺) So
Windows boot menu appears. Choose Safe Mode, then
process will run until the end display options
user should use to get into Windows safe
mode. In Windows XP, the account will usually appear
Administrator and the accounts we have. Choose an ordinary user account
we use.
After that, usually we'll be asked whether to go into Safe mode mode
or are we going to use Windows system restore facility. Click Yes, then
we will go into Windows safe mode mode. That is, Windows will actively
with the device it is (minimum standard).
Active in Safe Mode
There is a Windows registry subkey that is useful to run a program
automatically when Windows is turned on. So, if we want to be a file
Executable active when Windows is turned on, then we must write the subkey
This autorun with a value name that contains data that says
that X. EXE file is a file that should be executed. X here represents
any EXE file name.
Standard tools to check the configuration of Windows autorun is
System Configuration Utility program or better known as MSConfig
because the file launcher program called msconfig.exe. To call him,
done via the Run command from the Start menu. Click Start - select Run and
type in msconfig. Press Enter or click OK.
System Configuration Utility window will appear and seen a few tabs.
One of the Startup tab. Tabs are useful to see what programs
which will be run by Windows when Windows is activated. This is it!
The virus usually will block the use of this program. Whether it's with
Run or monitor turning off the option caption (title / name) of the program window
The currently active. If the caption programs that are active is equal to
caption that has been targeted by the virus, the virus will soon be automatically
shut it down or maybe do a reboot. Now you know.
automatically when Windows is turned on. So, if we want to be a file
Executable active when Windows is turned on, then we must write the subkey
This autorun with a value name that contains data that says
that X. EXE file is a file that should be executed. X here represents
any EXE file name.
Standard tools to check the configuration of Windows autorun is
System Configuration Utility program or better known as MSConfig
because the file launcher program called msconfig.exe. To call him,
done via the Run command from the Start menu. Click Start - select Run and
type in msconfig. Press Enter or click OK.
System Configuration Utility window will appear and seen a few tabs.
One of the Startup tab. Tabs are useful to see what programs
which will be run by Windows when Windows is activated. This is it!
The virus usually will block the use of this program. Whether it's with
Run or monitor turning off the option caption (title / name) of the program window
The currently active. If the caption programs that are active is equal to
caption that has been targeted by the virus, the virus will soon be automatically
shut it down or maybe do a reboot. Now you know.
why, is not it? Why when a virus is active, and we called msconfig,
suddenly msconfig program window closes by itself. Or perhaps,
suddenly, the computer reboot
suddenly msconfig program window closes by itself. Or perhaps,
suddenly, the computer reboot
 |
| Tab Startup msconfig |
On the Startup tab, Startup items will be visible column, which shows the name
items that will be run when Windows is activated. Also the command column,
which typically contains programs that are activated plus its parameters if any.
While the Location column, showing the location of the subkey (nerve) registry
store this data set. In the example shown, the name turned out to be SMTray
belongs to a program called SMTray.exe and are in the folder d: \ Program
Files \ Analog Devices \ SoundMAX.
The virus will usually make a value here, so files that trigger activating
program is executed when booting Windows happening so research in
This part is very important to do. Unfortunately again, the viruses now
pair the name of the item with the name of "smell-the smell of" the name of the file system
Windows. This is to trick the user who checked it. For example,
with the name windows.exe, svc0host.exe, rundlll.exe and others.
Here is our foresight that determines the success or failure to recognize the virus file.
And it needs to exercise
items that will be run when Windows is activated. Also the command column,
which typically contains programs that are activated plus its parameters if any.
While the Location column, showing the location of the subkey (nerve) registry
store this data set. In the example shown, the name turned out to be SMTray
belongs to a program called SMTray.exe and are in the folder d: \ Program
Files \ Analog Devices \ SoundMAX.
The virus will usually make a value here, so files that trigger activating
program is executed when booting Windows happening so research in
This part is very important to do. Unfortunately again, the viruses now
pair the name of the item with the name of "smell-the smell of" the name of the file system
Windows. This is to trick the user who checked it. For example,
with the name windows.exe, svc0host.exe, rundlll.exe and others.
Here is our foresight that determines the success or failure to recognize the virus file.
And it needs to exercise
If we've found an item that we suspect, remove the checkmark
that is in front of the startup items. If not checked, it means the item is not
will be executed at boot time. Conversely, if unchecked, it will
is run. After we did the check or un-tick click
OK and reboot to do the conversion process becomes active.
Belong to any other standard Windows tools that can be used to check
autorun configuration registry is Registry Editor program. To call him,
done via the Run command from the Start menu. Click Start - select Run and
type regedit. Press Enter or click OK.
Program registry editor will appear. Go to location:
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ CurrentVersio
n \ Run
that is in front of the startup items. If not checked, it means the item is not
will be executed at boot time. Conversely, if unchecked, it will
is run. After we did the check or un-tick click
OK and reboot to do the conversion process becomes active.
Belong to any other standard Windows tools that can be used to check
autorun configuration registry is Registry Editor program. To call him,
done via the Run command from the Start menu. Click Start - select Run and
type regedit. Press Enter or click OK.
Program registry editor will appear. Go to location:
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ CurrentVersio
n \ Run
Repeatedly double-click the subkey that looks so these locations
was found.
 |
| Location to be examined |
On the Run subkey is usually the virus will write the name of a new value for
activate the virus program. To delete the existing data, click the value name
and press DEL.
Other locations that we need in order to check this registry autorun
are:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Once
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
OnceEx
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
If found the name of the value that you think are strange, delete it ...
From some of the subkeys above, there is a subkey that is quite special. namely
RunOnce subkey. Unlike the Run subkey that will always run
program is in it every time Windows is turned on, the subkey
RunOnce is typically used to run a program as much as one
time only! So, this subkey is usually used by a program to enable
the process as much as one-time only, so the name is written down value
here will only apply one time only. Once executed, the value name
will be deleted.
If the virus is quite naughty, he will create a virus program for writing
pengaktifnya in this subkey. Thus, the virus will be active when the computer is turned on.
The program will be run and the name of the trigger value will be deleted. then
he did not leave a trace in msconfig. After a time when the virus is active,
he will make the program a timer that periodically re-write the name value
in the subkey. Or maybe the virus will only write the data on
RunOnce subkey when the computer will be logged off. That way, the virus
will be maintained existence. Pretty clever ', right?
But .... There are even crazier ... ☺ RunOnce subkey with the help of this, the virus
would still be alive even if Windows is run in SAFE MODE mode!
The trick? It's simple! Namely by adding a certain character
on behalf of such value, then the virus will be run in safe mode.
Character is it? I will not tell you☺ heheh!
I think builders will hide the science anymore.
We direct the practice, yes? Call Regedit and go to the subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Once
We create a value named COBA's name. The name of this value for example
will call the virus file named VIRUSKU.EXE
 | |
| Location of the target subkey. |
Right-click the RunOnce subkey. Context menu will appear, select New, select
String Value.
 |
| Create a new subkey |
A new subkey will appear. Let's change the name value with the data
COBA. Type in COBA and press Enter
 |
| Create Name Value |
Double-click the value name, and we fill it with data
c: \ windows \ virusku.exe. Then click OK.
 |
| Fill in the name value |
If correct in doing so, we will have the name value with the COBA
type string and has the data c: \ windows \ virusku.exe. That is, when later
Windows is enabled, the file VIRUSKU.EXE will come running!
 |
| Name the new value |
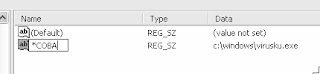
Now, how do you get the name value will still be
even run Windows included in SAFE MODE mode?
Easy! Simply add the character * (asterisks) in front of the name value.
That is, we replace with the name of COBA COBA name *
 |
| Change the name of the name value |
If you do not believe, do the boot and log in SAFE MODE mode.
Saharusnya VIRUSKU.EXE file with the name will still be run by
Windows. If we attach the file is a real virus file, then
consequences will be quite fatal. Virus will still be present in memory even if we have
mode using SAFE MODE. Even though this trick seems simple, but
quite dangerous if used. Because after the data is executed, then
run data will be deleted by Windows. so that will
complicates tracking the source of the problem. Take care ...!
If the virus remains active even if we had entered into
mode safe mode, check the RunOnce subkey is
over and over again. Who knows the virus is not the technique used by shell
spawn, but rely on the RunOnce subkey.
RunOnce this technique, it is still rarely done by the virus.
So, the obligatory pairing! The more
manipulation that can make the virus is active, it will
the more successful the virus survive. Viva Virus
Alternate Shell Safe Mode
The virus usually will not be active when we go into safe mode. That's usually!
In its development, the virus was also already started to widen
wings, grabbed (cease-and-desist .. ☺) some handling safe mode
by pairing the trigger file on some registry subkey. with
In this way, the virus will still be run and prevent users to enter
SAFE mode mode! Rude indeed! But yeah ... so .. my dear .. hehehe
☺
So, this trick will fulfill the first trick was to add intricately ... ☺
shutdown virus. Hehehe ... pa pa ndak even added fun, right?
Location attacked registry subkey is:
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet001 \ Control \ safeboot
 |
| Location of the target subkey |
AlternateShell. With its data type is string. We'll see the default field
is cmd.exe. If it does not contain such data, it is possible that the file
there is a file virus. Beware!
Suppose it happens, double click the value name and the Value field
change to the data contains cmd.exe. Click on OK. Wrong!
 |
| Editing data entries |
That need attention! Viruses are generally also will attack subkeysubkey
are similar. The meaning is this ... will attack the virus is also the location of the registry
else that stores data safeboot, usually there are more than
one of these controls. Other locations are under attack are:
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet002 \ Control \ safeboot
HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet003 \ Control \ safeboot
So, depending on how the computer has a subkey
ControlSet00X. X here represents the numbers 1, 2, and so on. by turning the
data on behalf AlternateShell value, then the computer will usually
failed to get into SAFE MODE, instead running a virus file!
If a virus attack and we fail to go into safe mode
mode, then the alternate shell subkey, this subkey must we
check out. If the data content strange, not standard, then change
filling with cmd.exe.
Despite this manipulation seem harsh and cruel, but
what can make, interception go into safe mode, shall
carried out. Because it will make the virus more secure and
maintained its existence!

 5:40 AM
5:40 AM
 Unknown
Unknown


0 comments:
Post a Comment